Proxy IP Beginner's Guide: What Is a Reverse Proxy?

When encountering proxy IPs, server deployment, or website architecture, many people come across the term "reverse proxy." It is primarily an infrastructure that serves websites and servers. This article will focus on the basic concepts, working principles, and common use cases of reverse proxies, helping you gain a clearer understanding of this concept.
Proxy Basics
In networks, the core function of a proxy is quite simple—it adds an intermediary layer between the request initiator and the target. The real difference lies in which side this intermediary stands: whether it initiates requests on behalf of the user or receives requests on behalf of the server. Because of the different positions and roles, proxies are classified into two fundamentally different modes: Forward Proxy and Reverse Proxy.
What is a Reverse Proxy?
A reverse proxy is a proxy mechanism deployed on the server side, mainly used to receive requests from users on behalf of backend servers and forward these requests to the servers responsible for handling business logic. To users, the access process is transparent and appears as normal access to a website; however, in the actual architecture, user requests first reach the reverse proxy server instead of the backend server providing the business service directly.
How a Reverse Proxy Works
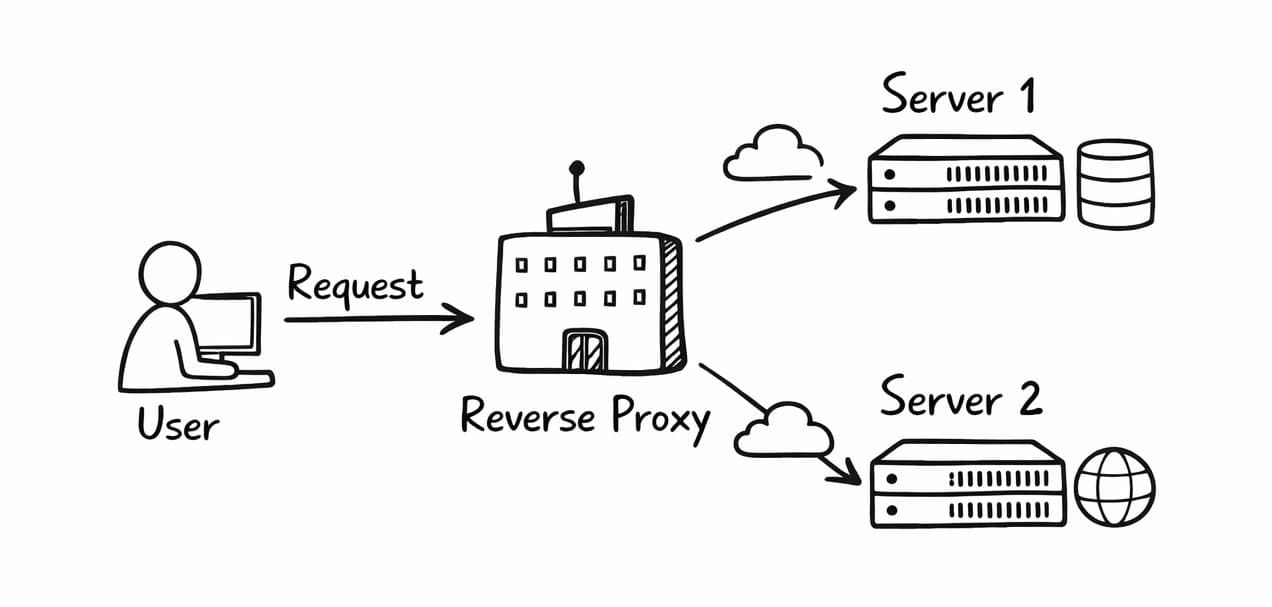
A typical reverse proxy access flow is as follows:
1. The user visits www.example.com in the browser.
2. The request first reaches the reverse proxy server (e.g., Nginx, Cloudflare).
3. The reverse proxy forwards the request to backend servers (A / B / C) based on predefined rules.
4. The backend server returns the data.
5. The reverse proxy returns the result to the user.
The entire process is completely transparent to the user.
Users neither know how many backend servers exist nor the real IP addresses of the servers.
What Problems Does a Reverse Proxy Solve?
1. Hide the Real Server IP and Improve Security
Specifically, backend business servers are not directly exposed to the public network; all user requests first pass through the reverse proxy server. Thus, hackers or attackers only see the IP of the reverse proxy and cannot attack the actual business server directly. Even if the backend server’s IP address is accidentally leaked, it can be quickly switched by changing the reverse proxy configuration, thereby reducing risk. This is why many large websites and services use reverse proxy architectures.
2. Load Balancing to Support High Concurrent Access
Reverse proxies can distribute user access requests across multiple backend servers, preventing a single server from bearing excessive load. This load balancing not only improves the overall system's processing capability but also ensures website stability during high traffic periods. Common distribution methods include round-robin, weighted distribution, and least connections. Without a reverse proxy, many large websites would struggle to provide stable and efficient service.
3. Speed Up Access and Reduce Server Pressure
Reverse proxies can also perform many "intermediate optimization" tasks, such as caching static resources like images, CSS, and JavaScript files to reduce repeated requests reaching the backend servers. Additionally, reverse proxies can serve content from nearby nodes to improve user website access speed—this is essentially the core of Content Delivery Networks (CDN).
4. Unified Management of HTTPS, Security, and Rules
Reverse proxies often take on important roles like unified deployment of HTTPS certificates, automatic redirection of HTTP requests to HTTPS, rate limiting, anti-scraping and Web Application Firewall (WAF) protection, as well as logging and access control.
Reverse Proxy vs Forward Proxy
Forward Proxy (Proxy IP)
Usually requires users to configure it themselves. Mainly used to hide real IPs, help cross-regional access, or conduct account operations and data collection. Most residential and data center proxies you buy are forward proxies.
Reverse Proxy
Stands on the server side. Mainly used to support website architecture, enhance security protection, and improve access performance.
Comparison Table
| Comparison Item | Forward Proxy | Reverse Proxy |
|---|---|---|
| Proxy Target | User | Server |
| Deployment | Client-side | Server-side |
| Requires Setup | Yes | No |
| Changes User IP | Yes | No |
| Common Uses | Bypassing geo-blocks, privacy, proxy IP | Load balancing, security, acceleration |
Who Can Use Reverse Proxy?
· Website owners / Developers
· API service providers
· SaaS / Platform products
· High concurrency business operators
· Enterprise IT / Operations personnel
Summary
As a critical infrastructure on the server side, reverse proxies play an indispensable role in modern network architecture. They can effectively hide real server IPs, enhance system security, distribute access pressure through load balancing, and ensure website stability. At the same time, reverse proxies can accelerate access experience, unify the management of security certificates and access rules, and simplify server operations. Understanding the working principles and application scenarios of different types of proxies helps design and maintain efficient and secure network services.







